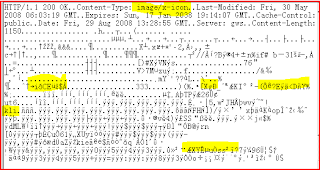
It has made the round that this devilish eye mutates the time of windows you can also observe this action when you start analyzing network packets and when you take a look to the cookie dates. If you see 1990 something is wrong, I don´t know why they have such a affinity to this year as well as to dates that lies far in the future like 2015, 2038, 2096, 2100. One possibility could be their hidden filesystem that probably relies on that date mutation.
 The other possibility for 1990 is the establishment date of All Seeing Internet Eye according to "MatrixArch", for 18 years in existence. Their allusions to the movie Matrix is clearly to see, as they seem to have chosen me as (one of their) Neo(s;)) there is no wonder that you will see the name many times in this hidden mutant filesystem which also affects advapi32 (known as the ultimate cia backdoor), probably also a sort of HPA(Hidden/Host Protected Area) some may also call it (S-)ATA protected area. FYI: It affects USB drives and sticks too. Beside according to wikipedia DBAN does not delete HPA! Originator of HPA is Phoenix and it is unavailable for all operating systems, such as Windows and Linux, if secure mode is enabled by whatsoever. (usually by bios)
The other possibility for 1990 is the establishment date of All Seeing Internet Eye according to "MatrixArch", for 18 years in existence. Their allusions to the movie Matrix is clearly to see, as they seem to have chosen me as (one of their) Neo(s;)) there is no wonder that you will see the name many times in this hidden mutant filesystem which also affects advapi32 (known as the ultimate cia backdoor), probably also a sort of HPA(Hidden/Host Protected Area) some may also call it (S-)ATA protected area. FYI: It affects USB drives and sticks too. Beside according to wikipedia DBAN does not delete HPA! Originator of HPA is Phoenix and it is unavailable for all operating systems, such as Windows and Linux, if secure mode is enabled by whatsoever. (usually by bios)